UMR network security interest group performs wireless security audit
Posted by news
Wireless networks are spreading into many homes in America; however, many of these networks are insecure. A group of students from the University of Missouri-Rolla recently conducted an audit of the area’s wireless networks to evaluate the community’s wireless usage and to educate those with insecure networks.
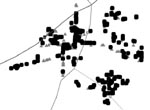 |
| A map of wireless security trouble spots in the Rolla area. The dark squares symbolize open networks and light triangles symbolize secure networks. |
 |
| Members of UMR SIG Security Group. |
In November the UMR chapter of the Association of Computing Machinery (ACM) Special Interest Group Security (SIG Security) conducted a security audit of the wireless networks in use throughout Rolla.
SIG Security was broken into four teams in an attempt to audit the Rolla community during the span of one hour and 15 minutes. The audit relied on data gathered from wireless networks that publicly broadcast their identities. Only elements of data that wireless access points make public were recorded.
"There was no connection sniffing (for actual data being transmitted), password cracking or use of the networks during the audit," says Dr. Daniel Tauritz, assistant professor of computer science at UMR and advisor of the SIG Security group. "But this isn’t to say that such things couldn’t occur at the hands of less responsible individuals," warns Joshua Maib, a senior in information science and technology from Kansas City, Mo. and SIG Security co-chair.
When the data from all four teams was pooled together and analyzed, SIG Security had recorded 589 unique wireless networks throughout Rolla. Of these, roughly 44 percent were protected, but the remaining 56 percent were completely insecure, says Jason Trent, a graduate student in computer science from Nixa, Mo.
In response to its audit results, SIG Security suggests the following security practices:
To decrease the strength of the radio signal outside your intended coverage area, position wireless components away from windows and toward the center of your home. Avoid placing the wireless components near electrical equipment that can cause signal interference, like microwaves or cordless telephones.
Enable encryption such as Wired Equivalent Privacy (WEP) at the strongest complexity the device offers, or if available, the much stronger Wi-Fi Protected Access (WPA) protocol. "WEP is the most prevalent security implementation with wireless networking," says Tauritz. WEP authenticates anyone who wants to access your wireless network and encrypts or disguises any traffic it produces. "WEP/WPA must be configured on the access point (router) and each client (desktop, laptop, PDA etc.) that you expect to use on your network. The steps to enable WEP vary between hardware and software manufacturers, but are outlined in detail in owner’s manuals and at websites produced by the manufacturer of your wireless devices."
If your network consists entirely of notebooks and desktops, try disabling broadcast of the network’s Service Set Identifier (SSID). However, some devices such as cell phones and PDAs do not function properly without SSID broadcasts. "Your SSID is the identifying name assigned to your network, and is regularly transmitted in the open air to advertise its existence," Maib explains. "Stopping this process requires a client to know the SSID of his or her access point before connecting to it," says Laura Woodard, a sophomore in computer science from Manhattan, Kan. "An easy way to check and see if your SSID is broadcasting is to download netStumbler from www.netStumbler.com. This program will only be able to see networks that have the SSID broadcasting; it will not show passwords or even connect to an open broadcasting network. If your broadcast is off, it will not be found by netStumbler."
Disabling broadcast of SSID does not increase security, nor is it intended to. Instead, it reduces visibility and is an extra step to inform outsiders that the network is not open for their use. Because SSID is sent unencrypted in packets to authorized third parties, an attacker could use sniffing tools on a connection between the access point and an authorized third party to circumvent disabled broadcasts. Disabling SSID broadcast without enabling methods of encryption or authentication is futile.
Some of the problems encountered with networks that are not protected by encryption and its SSID broadcasting can not only be annoying, but can be dangerous, Tauritz warns.
One reason to discourage the public from using your network is that "with access to your wireless network, anyone with a laptop computer and a wireless card can use your internet connection to send spam email, or even break into another computer through your internet connection," Woodard says. "And if caught, you would get the blame because it would be traced back to your network and computer, not the actual culprits." Trent adds, "Enabling encryption and disabling SSID makes it clear to outsiders that your network is not for public use."
SIG Security encourages those with or considering the use of wireless networks to follow the recommendations outlined here. "Simple preventative steps now may save you from complex headaches in the future," says Tauritz.
The group assumes the majority of wireless users aren’t aware of their security problem and don’t intend to share their service; however, in the audit, SIG Security found several locations that don’t mind sharing their wireless access points with the public. "Rolla has a few hotels currently advertising their open access wireless points," Woodard says. "If you are willing to share your wireless access point let the public know, it is great advertising!"
ACM SIG Security is a group of UMR students that meets biweekly to discuss computer and network security issues. The group’s goal is a more universal acknowledgment and employment of security in relation to technology.
Microsoft Windows users can determine if their computers are WEP enabled by following these quick steps:
Click the Start button and choose Settings, and then Control Panel. From the Control Panel, double-click the icon labeled Network or Network Connections. In the box that appears, double-click on the icon corresponding to your wireless device.
Click on the Advanced or Change Advanced Settings tab and a list of properties should appear.
Click on the Wireless Networks tab.
With your network highlighted, click the Properties button.
Under Data Encryption there is a choice of WEP or disabled. If disabled is selected and no password is listed in the network key box, WEP must be enabled through the Access Point Settings dialog box.